Mobile Application Security Testing/ Assessment simulates attacks to test an app's security and identify mobile app security risks, accelerate remediation, & prevent future attacks.
Mobile applications are widely used by businesses today to provide a seamless workplace and customer experience. They could be business applications for banking, healthcare, m-commerce, and other industries.
A mobile app's security is tested or assessed by simulating how a malicious attacker would choose to take advantage of the app's current security defects. You can use the assessment to determine whether your mobile application is ready for production. To ensure that problems are found before going live, the testing process considers both code and configuration flaws in a production-like environment. This prevents your mobile app and organization from severe impacts, including privacy violations, reputational damage, and penalties from compliance authorities and regulators.
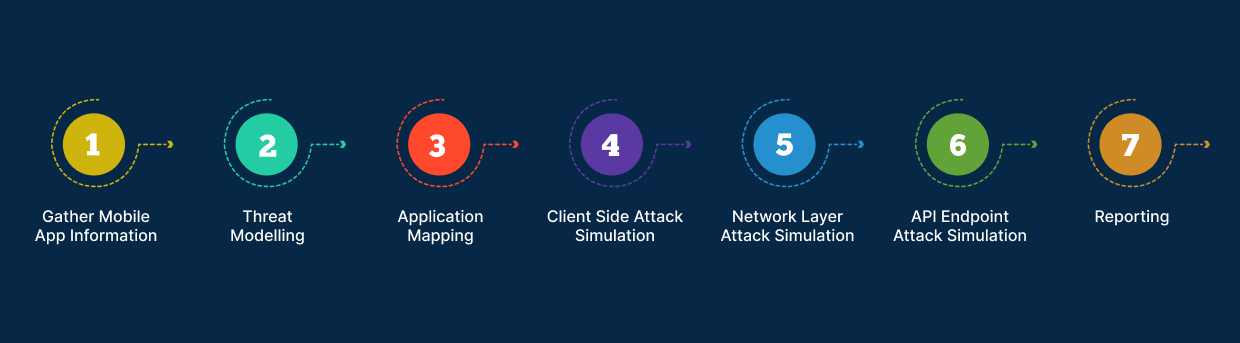
The following are phases of the mobile app testing to ensure that your apps, and your users' personal data are protected:
Gather Mobile App Information - Our team gathers information about the app's architecture, the business use cases the app serves, the business logic in which the app operates and other relevant information about the mobile application.
Threat Modelling - Create a threat profile of the application by listing all its entry points, features, and data stored or handled; At rest / In use / In transit, by the mobile app. It allows testers to design specific test plans to stimulate attack scenarios that may result in analysing actual risks rather than general weaknesses.
Application Mapping - Based on information from the previous phases; source code and application scanning is done to look for known and common vulnerabilities such as Improper Platform Usage, Superfluous Data Storage, Exposed Authentication, Insecure Communication, Malicious Third-Party Code, Lack of server-side controls, Client Side injection flaws, etc.
Client Side Attack Simulation - Key focus areas of client-side attack simulation are:
Network Layer Attack Simulation - Hackers often target the communication between clients and backend APIs and our focus on common network vulnerabilities for mobile app traffic are
API Endpoint Attack Simulation - APIs serve as the foundation for service and microservice architectures and hence make them very attractive to attackers. We test for common attacks against mobile app APIs
Reporting - The Mobile Application Security Testing Report includes:
Mobile app security testing is a necessity in the current fast evolving threat landscape and the benefits are:
1. Enables you to conform your app to industry standards or compliance requirements.
2. Increases the trust that your customers have in your offerings (when your app is ISO 27001 certified, for example).
3. Helps you identify and comprehend security flaws so you can fix them and be ready for risks like security breaches.
4. Reduces the financial and reputational consequences associated with security incidents.
5. Helps you decide which components of your app's ecosystem to change: your own code, third-party code, or platform.