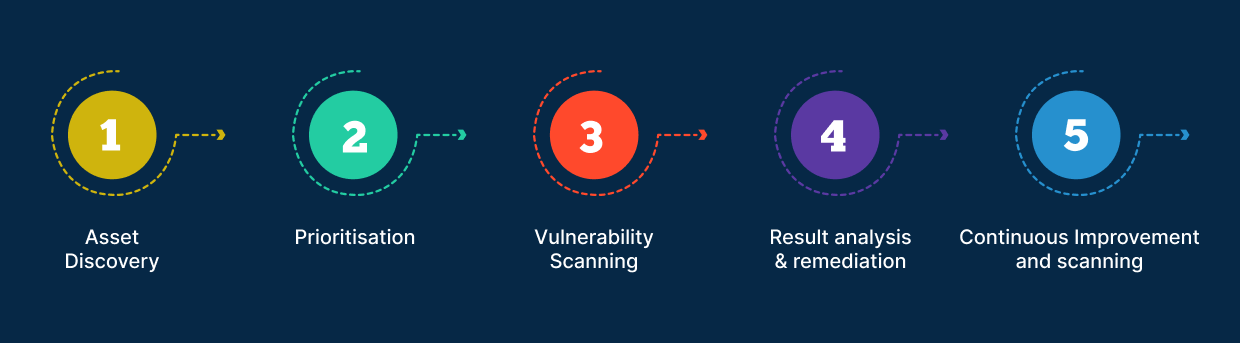
Hackers are constantly search the internet for vulnerabilities, therefore if you don't want your company to become a victim, you need to be the first to identify these openings. To manage your vulnerabilities effectively, you must take a proactive strategy, and doing a vulnerability assessment is an essential first step.